Declined
Last Updated:
03 Apr 2024 15:24
by Sagar
Sagar
Created on:
01 Apr 2024 18:08
Category:
UI for WinForms
Type:
Bug Report
Account Takeover
# Vulnerability Report: Account Takeover via Email Change Functionality
## Summary:
During security testing of the email change functionality on the Telerik website, it was discovered that the application can be vulnerable to an account takeover attack. The vulnerability allows an attacker to change the email address associated with an account to their own email address, effectively taking over the victim's account.
## Vulnerability Details:
- **Functionality Description:**
- The Telerik website provides a functionality for users to request a change in their email address.
- This functionality consists of two sections: current email and new email.
- The current email is not accessible from the user interface, while the new email can be inputted by the user.
- After inputting the new email and clicking the "Change Email" button, the user's request is processed.
- **Attack Scenario:**
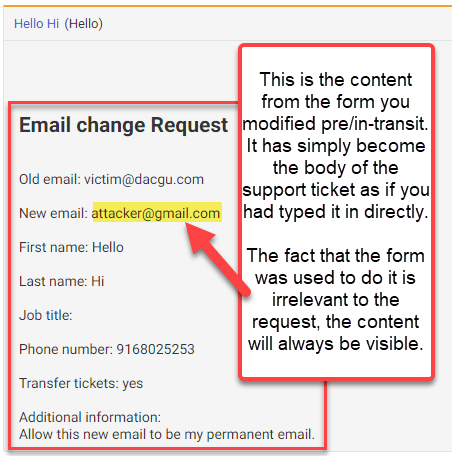
1. **Attacker Inputs Their Email:** The attacker inputs their own email address in the new email section.
2. **Intercepting the Request:** Using interception tools, the attacker intercepts the request before it is sent to the server.
3. **Modifying the Request:** The attacker modifies the request to replace their own email address with the victim's email address in the current email section.
4. **Consent Form Manipulation:** Additionally, the attacker can manipulate the consent form associated with the email change request to gain access to the victim's account without their consent.
5. **Changing the Email Address:** The modified request is forwarded to the server, resulting in the victim's email address being changed to the attacker's email address.
## Impact:
- **Account Takeover:** The vulnerability allows an attacker to take over the victim's account by changing the email address associated with it.
- **Data Access:** Once the attacker gains access to the victim's account, they may have unauthorized access to sensitive data and functionalities associated with the account.
## Mitigation Recommendations:
- **Input Validation:** Implement strict input validation to ensure that only legitimate email addresses are accepted in the new email section.
- **Consent Verification:** Require additional verification steps, such as email confirmation or user authentication, before processing email change requests.
- **Session Management:** Implement session management mechanisms to detect and prevent unauthorized access to account settings and functionalities.
- **Security Awareness:** Educate users about the risks of phishing attacks and social engineering tactics used by attackers to gain unauthorized access to accounts.
## Affected URL:
- Email Change Functionality: [https://www.telerik.com/account/support-center/email-change](https://www.telerik.com/account/support-center/email-change)
## Conclusion:
The discovered vulnerability poses a significant security risk to Telerik website users by allowing attackers to take over accounts through manipulation of the email change functionality. It is imperative for the development team to address this vulnerability promptly by implementing appropriate security controls and mitigations to safeguard user accounts from unauthorized access.
**Best Regards,**
Sagar Dhoot
## Summary:
During security testing of the email change functionality on the Telerik website, it was discovered that the application can be vulnerable to an account takeover attack. The vulnerability allows an attacker to change the email address associated with an account to their own email address, effectively taking over the victim's account.
## Vulnerability Details:
- **Functionality Description:**
- The Telerik website provides a functionality for users to request a change in their email address.
- This functionality consists of two sections: current email and new email.
- The current email is not accessible from the user interface, while the new email can be inputted by the user.
- After inputting the new email and clicking the "Change Email" button, the user's request is processed.
- **Attack Scenario:**
1. **Attacker Inputs Their Email:** The attacker inputs their own email address in the new email section.
2. **Intercepting the Request:** Using interception tools, the attacker intercepts the request before it is sent to the server.
3. **Modifying the Request:** The attacker modifies the request to replace their own email address with the victim's email address in the current email section.
4. **Consent Form Manipulation:** Additionally, the attacker can manipulate the consent form associated with the email change request to gain access to the victim's account without their consent.
5. **Changing the Email Address:** The modified request is forwarded to the server, resulting in the victim's email address being changed to the attacker's email address.

## Impact:
- **Account Takeover:** The vulnerability allows an attacker to take over the victim's account by changing the email address associated with it.
- **Data Access:** Once the attacker gains access to the victim's account, they may have unauthorized access to sensitive data and functionalities associated with the account.
## Mitigation Recommendations:
- **Input Validation:** Implement strict input validation to ensure that only legitimate email addresses are accepted in the new email section.
- **Consent Verification:** Require additional verification steps, such as email confirmation or user authentication, before processing email change requests.
- **Session Management:** Implement session management mechanisms to detect and prevent unauthorized access to account settings and functionalities.
- **Security Awareness:** Educate users about the risks of phishing attacks and social engineering tactics used by attackers to gain unauthorized access to accounts.
## Affected URL:
- Email Change Functionality: [https://www.telerik.com/account/support-center/email-change](https://www.telerik.com/account/support-center/email-change)
## Conclusion:
The discovered vulnerability poses a significant security risk to Telerik website users by allowing attackers to take over accounts through manipulation of the email change functionality. It is imperative for the development team to address this vulnerability promptly by implementing appropriate security controls and mitigations to safeguard user accounts from unauthorized access.
**Best Regards,**
Sagar Dhoot
Attached Files:
4 comments
Sagar
Posted on:
03 Apr 2024 15:24
ADMIN
Lance | Senior Manager Technical Support
Posted on:
03 Apr 2024 15:12
Sagar
Posted on:
02 Apr 2024 13:09
ADMIN
Lance | Senior Manager Technical Support
Posted on:
02 Apr 2024 12:39